Inductive Automation's Kevin McClusky suggests a different approach to make your industrial systems safe and secure in this month's featured guest blog.
What would it take to break into Fort Knox? As one of the most secure locations on the planet, it wouldn’t be easy. However, someone with the right amount of time, planning, and determination may be able to find a way.
The same is true for most industrial systems. So, how to protect what’s inside? Strategies that may work in the physical world—thicker walls or taller fences—don’t translate to digital systems. The tools of the trade here are a variety of high-tech solutions such as firewalls, SIEMs, IDS’s, and IPS’s. These are tools mainly to monitor network traffic and control the flow, and provide early alerts if there’s unusual activity.
However, what if we threw out all of those traditional tools and took a different approach?
Enter Zero Trust.
Zero Trust is a networking philosophy first coined over a decade ago, which has seen wide interest and significant adoption worldwide.
In a sentence, the concept behind Zero Trust is that your systems have no trust (zero trust) of anyone else on the network. Just because there’s a network connection doesn’t mean that the remote party connecting is a trusted user or system of the organization.
It’s basically a mindset shift that’s made a big difference in the industrial and IT world. It shifts the thinking from “secure the network” to “there are bad actors on the network, secure the data and devices.” It’s similar to a city with streets, houses, and commercial buildings. Rather than attempting to keep bad guys off the streets, there are locks to keep them from entering trucks and buildings and there are guards to only let in trusted associates.
This mindset shift requires the security to be on the devices/systems (buildings) and on the data transport (trucks).
Put another way, Zero Trust is an approach to cybersecurity that requires verification during every stage of digital interaction, even when those interactions take place on secure, permissioned networks. It may sound like a complicated process, but luckily securing each piece of your system can be made relatively easy with the right combination of hardware, software, and data transfer protocols.
Device Security
Securing your whole chain of communication can start at either end. We’ll start with the device at the edge of the network, doing data collection and communication with hardware. Edge devices often lack encryption or certificate support, so choosing a device built with security in mind may be required to fully secure your communication.
Built-in network traffic control can prevent incoming traffic by blocking anyone “at the gate” other than trusted communication. Using high security protocols like MQTT with exclusively outgoing connections paired with strong encryption can eliminate the routing of incoming traffic, further securing the device. A good example of edge devices in this category would be groov RIO and groov EPIC, which come with tools built in to help secure this communication.
When combining Zero Trust with traditional IT security approaches, strong network segmentation can also be a good idea with devices that support multiple network interfaces. Network zones can be configured where devices speak on two networks simultaneously: for example, a more secure sensor or controls network and a less secure company network. Network zones help ensure there’s no path between the two networks for network traffic to flow, even with the device connected to both networks. Data communications and controls can be sent between both networks through the device while keeping the actual network traffic only on the networks where it belongs.
Transport Security
One other important place to secure is the communication flow itself from a device to where that data will be stored. Each and every one of those lines must be individually secured to maintain protection for the system at large. One great protocol to get you to secure communication right away is MQTT. The Art of the Possible series has already covered how to quickly get started with MQTT and Sparkplug, but it’s worth examining why these standards provide industry-leading security.
One key advantage is that MQTT connections can be exclusively outgoing. This allows users to leverage internal firewalls on devices to block all incoming traffic to devices by default. Keeping traffic limited to outgoing traffic significantly helps in protecting from external actors.
Additionally, most MQTT brokers come with a trifecta of encryption, authentication, and authorization built in. When enabled, all data transferred with MQTT is encrypted and requires a client certificate specific to the device or server receiving that data. Any data transfer between publisher and broker or broker and subscriber is encrypted using SSL/TLS, and then authenticated with usernames and passwords. Additionally, most MQTT brokers support Access Control Lists (ACLs), which can limit user access based on topic. MQTT streamlines transfer security, protecting each block of data without the tedium of setting up separate security settings for each connection.
System Security
Once data is collected and transferred, it ends up in a central system which also needs strong security controls. Using a central system that has strong security built in is paramount, as security generally can’t be "bolted on" to a system very easily, and sometimes it can’t be added at all if systems are using insecure communication technologies, protocols, or technology frameworks.
The linchpin of Zero Trust is authentication and authorization. Authentication, which determines who is logging in, is accomplished either with traditional usernames and passwords, or using modern IdPs to support things like company universal login and two-factor authentication. Authorization determines privileges and allows for more granularity through assigned user roles that can be specific to data access and application functionality. Even when a client has both authentication and authorization, the data transferred will still be encrypted as long as encryption is enabled. In most cases, the encryption takes place before the authentication even starts.
One example of a central system that has very strong security tools built in is the Ignition platform, which is created by Inductive Automation. Full disclosure: I work for Inductive Automation. That said, in my opinion as an engineer, the toolset is very versatile and provides one of the widest ranges of ways to cover yourself and your organization in the industry.
Regardless of whether you use Ignition or not, here are the things to look out for:
- Ability to enable encryption (TLS 1.2 or TLS 1.3 and beyond).
- Ability to use Identity Providers (IdPs), enabling modern security features like 2FA, centralized credential access, and revocation of privileges.
- Ability to use high security protocols like MQTT, and the ability to support OPC UA’s stronger encryption options.
- Ability to bridge multiple networks and apply security policies based on zones.
- Interoperability and support for open standards.
- Security focus from the vendor, including track record of responses to vulnerabilities with a reasonable timeline for resolution.
Beyond that list are a few additional items that are pluses:
- Security disclosures and a culture of openness, paired with a commitment to responsible disclosure, going beyond what is government mandated.
- Mapping support for Identity Providers roles to internal system roles.
- Well-established support policy and timelines for which software versions are supported.
If we’re looking at Ignition specifically, a few additional features are worth highlighting quickly.
Inside the Ignition platform, just recently an Authentication Challenge was rolled out as part of Ignition 8.1.16 to more easily authenticate supervisor approval in keeping with 21 CFR Part 11.
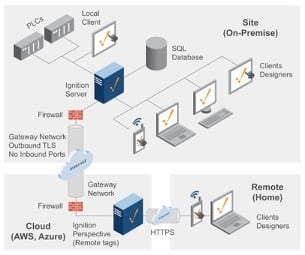
Ignition’s Gateway Network can also be used for secured bi-directional communication from central server to Edge, allowing outgoing connections from Edge to a central system, and providing tools like central management, remote alarm viewing and acknowledgement, remote upgrades, centralized backups, and advanced scripting in Edge Compute.
Other options exist for cloud-based data storage and secured connections. Ignition can transfer data into cloud services using cloud injector modules. Another cloud strategy is to deploy an Ignition server in AWS or Azure. This establishes a secured and encrypted single channel to that system that can be configured to be read-only, allowing clients to view remote tag data from the cloud while creating a locked-down environment that can satisfy both IT and OT.
Protect Your Data at Every Step
With the right combination of security-focused devices, protocols, and software, you will be in good shape on your journey for an end-to-end secure data collection and control channel.
And of course, monitoring the network is still a good idea. The SIEM, IDS, and IPS tools that IT has invested in still have a place. You could think of them like a police force for the streets. You want to make sure your buildings and vehicles are secure, but it never hurts to have someone looking out for you on the roads as well.
Learn more about how to make comprehensive security your system’s default setting by visiting the System Security page and the Security Hardening Guide at the Inductive Automation website.
— Kevin McClusky
Co-Director of Sales Engineering, Inductive Automation

