Inductive Automation's Kevin McClusky suggests a different approach to make your industrial systems safe and secure in this month's featured guest blog.
What would it take to break into Fort Knox? As one of the most secure locations on the planet, it wouldn’t be easy. However, someone with the right amount of time, planning, and determination may be able to find a way.
The same is true for most industrial systems. So, how to protect what’s inside? Strategies that may work in the physical world—thicker walls or taller fences—don’t translate to digital systems. The tools of the trade here are a variety of high-tech solutions such as firewalls, SIEMs, IDS’s, and IPS’s. These are tools mainly to monitor network traffic and control the flow, and provide early alerts if there’s unusual activity.
However, what if we threw out all of those traditional tools and took a different approach?
Read More
Topics:
Security,
cybersecurity,
Ignition,
Inductive Automation,
Art of the Possible
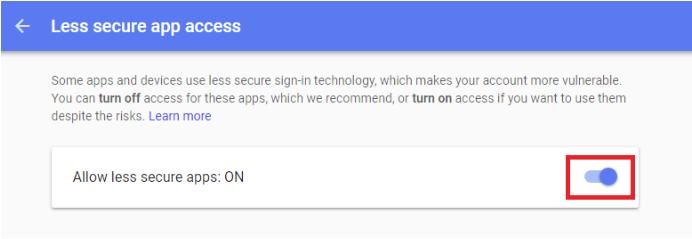
Prepare to make security changes to your email accounts by May 30, 2022.
For a long time, automation engineers have sent email alerts and reports from automation applications via a ‘throwaway’ Gmail account. This seemed harmless enough at the time and really useful, but it wasn’t very secure. As email abuse has risen over the years, it's time for the “less secure” party to come to an end.
Does this mean an end to all email alerts? Not at all. You just need to adjust your Google Gmail settings and update to a new application password in each application. Of course, this applies (with different end dates) to most other email providers as well as Google; check with your email provider for details. This blog will focus on Google Gmail.
Read More
Topics:
Security,
Node-RED,
groov EPIC,
snap pac,
groov RIO,
email notifications
Get help designing a secure industrial automation system with Opto 22's cybersecurity resources.
When you use groov EPIC or groov RIO products, you can rest assured you're getting cybersecurity ready products, right out of the box. There is even a groov EPIC Cybersecurity Technical Guide to help you design a secure system with step-by-step instructions.
With cybersecurity being one of the top concerns in today's industry, we decided it was important to address all your questions on security. We've put together several resources in a single location on the Opto 22 website to help you better understand your options when it comes to building the most secure control system possible.
Read More
Topics:
Security,
MQTT,
groov EPIC,
cybersecurity,
groov RIO
BDATA Solutions addresses the issue of Cybersecurity in IoT and Edge devices through blockchain technology.
With the recent well-publicized internet hacks, cybersecurity is unfortunately at the forefront of many people's minds. Our latest OptoPartner Video is timely, as BDATA Solutions uses Blockchain technology to address this issue in Industrial Internet of Things architecture.
Read More
Topics:
Internet of Things,
Remote monitoring,
IoT,
Security,
EPIC,
OptoPartner video
Best practices for cybersecurity and more from the groov EPIC v3.2 update to help you get sign-off on critical security upgrades.
Solarwinds, Oldsmar, Colonial, JBS—with all the cybersecurity news filling our inboxes, news feeds, and social channels, your customers may finally be ready to talk about a more rigorous security strategy.
So I figured this was a relevant time to share our recently updated tech note, “groov EPIC Cybersecurity Designs and Best Practices.” It details the mindset and specific actions that can change your automation from a security vulnerability into a security asset.
Read More
Topics:
Security,
groov EPIC,
cybersecurity
Terry Orchard is back in his studio to give you a video overview of the Secure Shell Access (SSH) feature on groov EPIC.
Whether you're already using Opto 22's groov EPIC or have been researching its features, it's important to note the extensive programming options it comes with. You can use the easy flow chart-based PAC Control, the familiar IEC 61131-3 compliant languages of CODESYS, or build Node-RED flows to move data.
But, did you know EPIC allows you to build your own custom applications using languages you know like Python, C/C++ and run them on an open, Linux®-based operating system? That's the topic of Terry Orchard's latest video, part of the new Opto 22 Developer series.
Read More
Topics:
Videos,
Security,
groov EPIC,
developer,
secure shell,
ssh
One of the new features in recent versions of the groov EPIC firmware (R1.4.0+) that hasn’t gotten much attention yet is the built-in virtual private network (VPN) client. I’m excited about it because it’s an incredibly rare feature in PLCs and PACs and makes it much easier to create a secure architecture for managing remote equipment.
Why? Because a VPN essentially creates a secure tunnel through the internet—using encryption and user authentication—that can connect remote EPICs to your PC or trusted company network. From a security and connectivity standpoint, it’s like the EPIC is on your desk or in your facility, protected in all the ways you protect your company network. Anything you can do with a locally networked device, you can do with a remote system using VPN.
Read More
Topics:
Security,
groov EPIC,
OpenVPN

The recent announcement of security vulnerabilities discovered in the Wind River® VxWorks® IPnet TCP/IP stack has prompted questions from Opto 22 customers about what impact this discovery may have on TCP/IP-based products developed and manufactured by Opto 22.
Opto 22 would like to reassure our customers that, after careful and thorough review, we can state that none of our hardware or software products contain the VxWorks IPnet TCP/IP stack or variants of that software and are, therefore, not directly exposed to any attacks that might target these vulnerabilities. This statement applies to the recent Opto 22 product family groov EPIC® (edge programmable industrial controller), the groov® Edge Appliance (groov Box), the SNAP PAC® System, and SNAP Ethernet I/O® products.
These security vulnerabilities, dubbed URGENT/11 by Armis, an enterprise IoT security firm that made the discoveries, have far-reaching implications and affect an extremely large array of industrial, medical, and enterprise environments. These include mission-critical systems such as SCADA, industrial controllers, PLCs, PACs, and more. Other systems outside traditional industrial devices like patient monitors and MRI machines, as well as firewalls, routers, modems, VOIP phones, and printers are also affected.
Read More
Topics:
PACs,
Security,
EPIC,
groov EPIC,
cybersecurity
As you might have read in previous blog posts, groov EPIC runs a Linux-based operating system that supports a variety of programming and operating options, including optional secure shell (SSH) access. SSH provides root access to the tools, software, and files on the groov EPIC system.
But how does SSH access work, what is it capable of, and is it right for you? In this post I’ll go into a bit more depth about secure shell and the Linux operating system (OS) on groov EPIC and provide answers to these questions.
Read More
Topics:
Security,
groov EPIC,
Linux,
secure shell
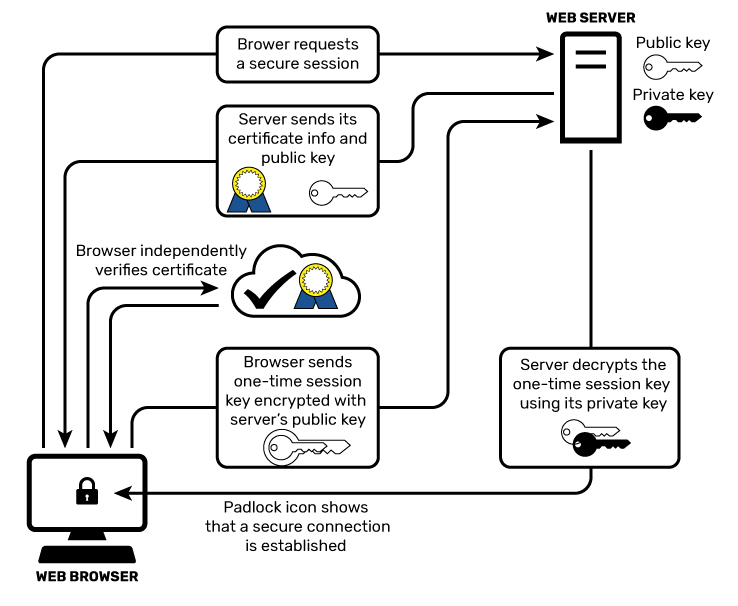
Go on, admit it. At some point in your life you've written down a password on a piece of paper in clear text. Anybody walking by can simply glance at your note, and they'll know what your password is.
No, you have never done that? Excellent.
But if you've ever used your web browser to log into a website over the web, and entered sensitive information like your password without encryption, you've effectively transmitted that information through the internet for all to see, almost like writing it on paper and showing it around.
Whoa.
Read More
Topics:
Security,
IIoT,
groov EPIC,
cybersecurity,
EPIC Security,
encryption,
EPIC Security Series