Tune in to the latest Manufacturing Hub podcast for insight on how to digitally transform today's plant floors and get valuable, secure data from legacy systems.
Most manufacturing plants aren’t greenfield facilities filled with brand-new automation. They’re a mix of legacy machines, isolated control systems, and manual processes that were never designed to support analytics or AI.
If you're looking for advice on bridging the gap of legacy automation systems to modern, data-ready operations without breaking what already works, then you'll want to listen to the recent discussion Opto 22's Benson Hougland had with the hosts of the Manufacturing Hub podcast, Vlad Romanov and Dave Griffith.
Tune in for some straightforward tips on how to digitally scale and access the right data from your systems.
Read More
Topics:
cybersecurity,
podcast,
digital transformation,
smart manufacturing,
manufacturing
Revisit the posts readers found most valuable on the OptoBlog in 2025.
Ready for another look back at highlights from 2025? Here's a chance to review the OptoBlog posts that resonated most with our readers this past year.
New ways to use Ignition software, staying current on firmware updates, strengthening cybersecurity practices, and picking up practical tech tips along the way: these articles reflect the challenges and priorities that OptoBlog subscribers are focused on.
Whether you’re revisiting a favorite or discovering it for the first time, here are the top five OptoBlog posts of 2025 that informed and guided this community.
Read More
Topics:
groov EPIC,
cybersecurity,
OpenVPN,
Ignition,
groov RIO
This cybersecurity video series demonstrates key product features to keep your systems safe.
Have you visited the Opto 22 video library lately? Along with product overviews and how-to videos, you'll find several developer videos.
If you've been wanting to know more about all the cybersecurity features that come with groov EPIC and groov RIO, then you'll want to see this video series that covers using self-signed certificates with your groov devices.
The goal is to ensure both trusted and encrypted connections—another way groov products deliver cybersecurity right out of the box. Watch and learn.
Read More
Topics:
groov EPIC,
cybersecurity,
certificate,
groov RIO
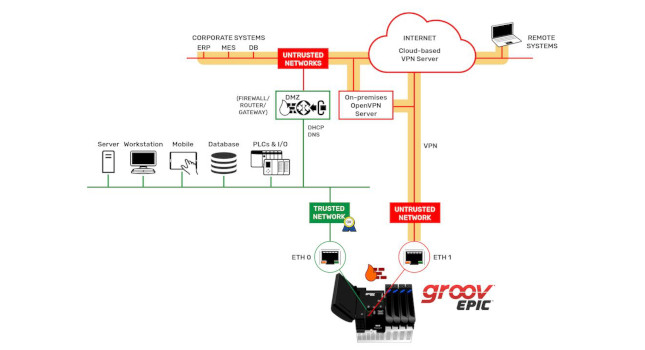
Learn how setting up VPN (virtual private network) configurations can help you securely connect to your remote devices.
In our latest video VPN configuration on groov devices using OpenVPN, you'll get a breakdown of the high-level configuration of VPNs and also a detailed walkthrough of the process.
But first, in this blog post, let's discuss the pain of secure remote connectivity and the gains that setting up a VPN can bring.
Read More
Topics:
groov EPIC,
cybersecurity,
EPIC Security,
OpenVPN
Process Control Dynamics joins the OptoChannel of distributors to share their industrial IoT expertise and focus on the groov family of products in Colorado and the Four Corners region.
Now you have more options when it comes to finding IIoT and critical infrastructure application solutions, especially in Colorado and the Four Corners region of the USA.
Meet Process Control Dynamics. They've helped thousands of customers implement technologically advanced and cost-effective solutions in a wide variety of applications and vertical markets since 1986.
Hear about their product experience and why they've added groov EPIC and groov RIO products to their portfolio.
Read More
Topics:
IIoT,
groov EPIC,
cybersecurity,
groov RIO,
OptoChannel
Are you struggling to get your systems on the network with your IT department? Here are some insights on designing a cybersecure controls system that an IT department will know and trust.
The simple action of picking up your cell (mobile) phone and making a call belies the enormous amount of work that goes on behind the scenes to get the protocols and encryption standards approved—so that each phone can connect to the cellular network securely.
If we homemade our own cell phones, it's understandable that the network provider would (and should) quickly become “the department of no,” not allowing us to connect to their network. Many things could go wrong, and they would soon be on the hook for any issues our device might cause.
It really is no different from when we show up at the factory with an Ethernet-enabled PLC and ask our IT department to connect it to the factory network.
They don’t know anything about the PLC! And they have lots of questions...
Read More
Topics:
groov EPIC,
cybersecurity,
groov RIO
Join Opto 22 and our technology partner Inductive Automation at the 7x24 Data Center event.
Is your facility mission-critical, with reliability needed 7x24? Then we hope to see you at the 7x24 Data Center Conference—happening next week in Orlando, Florida, June 9-12, 2024.
This conference is designed for anyone involved with 7×24 infrastructures: IT, data center, disaster recovery, cyber security and network/telecommunication managers, computer technologists, facility or building managers, supervisors and engineers.
Read More
Topics:
Events & conferences,
cybersecurity,
Ignition,
Inductive Automation,
data center
Opto 22's Director of Technical Marketing, Dan White, explains the features and importance of modern edge devices in this new Control Engineering article.
The industrial automation industry is now being driven by the idea of digital transformation and the industrial internet of things (IIoT). Understanding the concepts of edge and cloud technology and how they relate is becoming a necessity.
Opto 22's Dan White does an excellent job of explaining these terms and what it means for you and your future designs and applications. He shares his insights on edge devices, data management and cybersecurity in this newly published article from Control Engineering, "Edge to cloud: Understanding new industrial architectures."
Read More
Topics:
MQTT,
groov EPIC,
cybersecurity,
edge computing,
control engineering,
cloud computing
Beyond data transactions, understanding the relationship between clients and servers plays a significant role in cybersecurity.
What makes a device fill the role of a server or client? And, more importantly, how can you use that information to strengthen your network security and mitigate insecurities?
The best place to start with this topic is to loosely define what makes software act as a server or as a client. But throughout this blog, keep in mind that the two are not mutually exclusive—some devices can be both a server and a client. When playing the role of a server the key trait is that the server device is always listening.
Read More
Topics:
groov EPIC,
cybersecurity
See how Zendal overcame multiple challenges of cybersecurity, incompatible equipment, lockdown, logistics, and remote teams.
During the year 2020, dozens of companies worldwide worked to develop vaccines for the pandemic-causing virus COVID-19. Biofabri, a subsidiary of Spanish international biopharmaceutical group Zendal, became responsible for industrial production of the antigen vaccine for most of Europe.
Their task was daunting. Somehow they would have to construct and automate a new fill-and-finish facility during a worldwide pandemic, in a country with one of the strictest lockdowns. Logistics were soon in chaos, with even basic supplies unavailable. Zendal had a variety of older equipment in place with incompatible controllers and individual HMIs. They also had no control over the make or model of PLCs that package suppliers would provide with new equipment.
And towering over all other problems were issues of cybersecurity.
Read More
Topics:
Case studies,
Ignition Edge,
groov EPIC,
cybersecurity






-1.jpg)