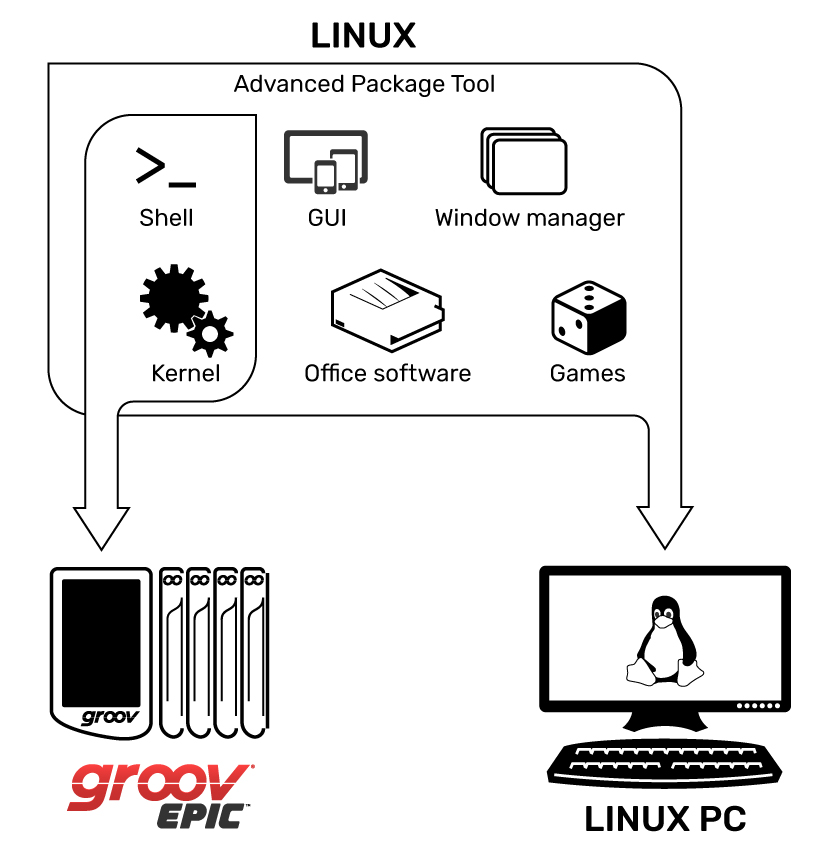
The OS, or operating system, of groov EPIC is very different from traditional controllers. Instead of a proprietary OS, EPIC uses an open-source Linux® operating system.
From a security standpoint, an “open source” OS sounds scary. But in many ways it is more secure than a closed-source one, especially a well-known and often-attacked OS such as Microsoft® Windows®.
Read More
Topics:
EPIC,
groov EPIC,
EPIC Security,
Linux,
secure shell,
ssh,
EPIC Security Series
Go on, admit it. At some point in your life you've written down a password on a piece of paper in clear text. Anybody walking by can simply glance at your note, and they'll know what your password is.
No, you have never done that? Excellent.
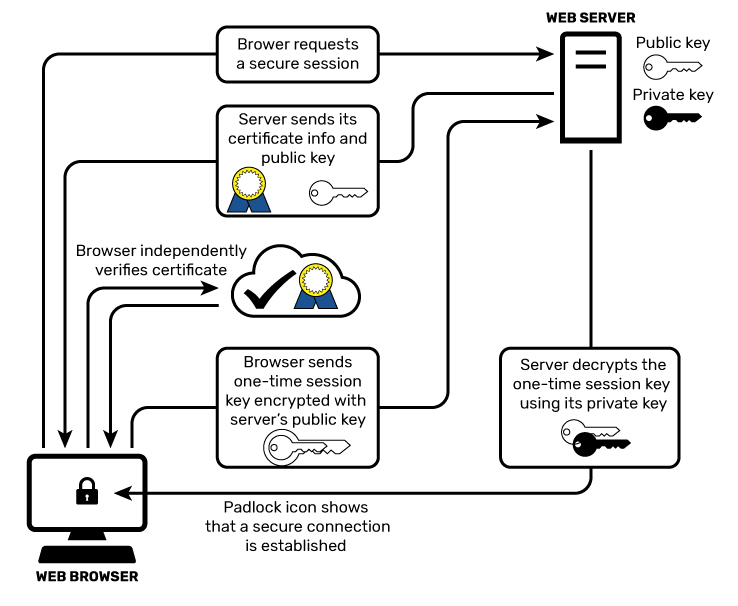
But if you've ever used your web browser to log into a website over the web, and entered sensitive information like your password without encryption, you've effectively transmitted that information through the internet for all to see, almost like writing it on paper and showing it around.
Whoa.
Read More
Topics:
Security,
IIoT,
groov EPIC,
cybersecurity,
EPIC Security,
encryption,
EPIC Security Series
In this blog post, let’s take a closer look at user accounts on the groov EPIC system, and how you can improve your system security by giving users and services fine-grained access to applications running on EPIC. In other words, make sure each person or service has only the access they really need and nothing more.
But before we get deep into user accounts, let’s first discuss user account credentials. Take a moment and ask yourself the following questions:
- Do you use the same password for multiple accounts?
- Do you use a mix of punctuation and capital letters in your passwords?
- Do you use long phrases as your passwords?
Read More
Topics:
Security,
groov View,
groov EPIC,
groov Manage,
cybersecurity,
EPIC Security,
User Accounts,
EPIC Security Series
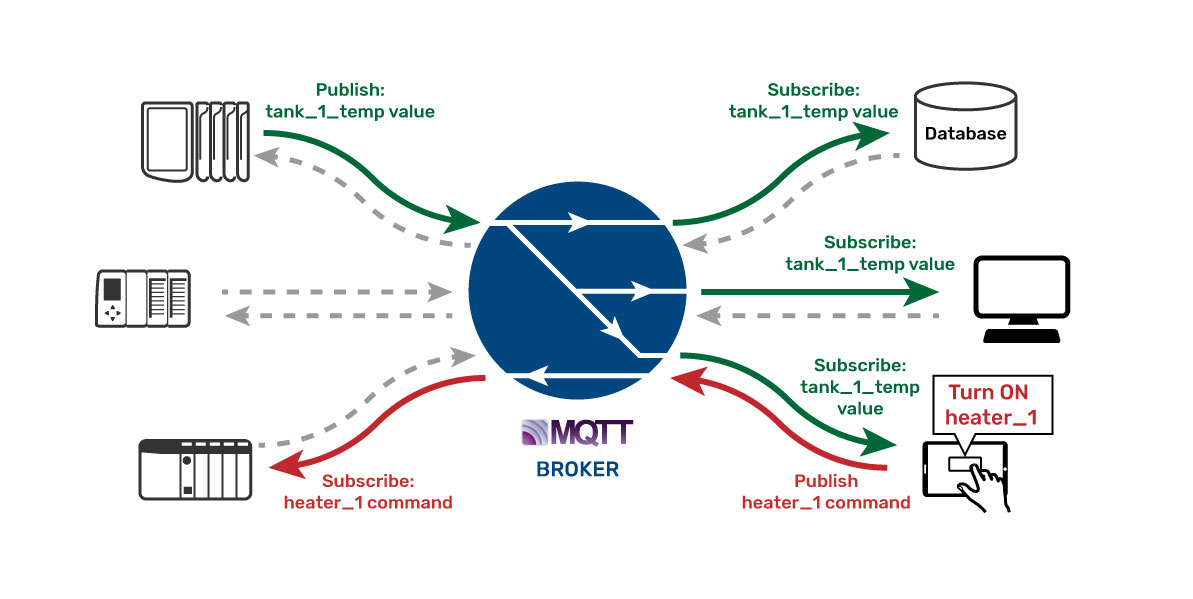
The story goes that a valve manufacturer wanted to have their networked smart valves certified for use in a nuclear reactor plant. The smart valve could report all sorts of critical data points to a database system and also be controlled by that SCADA system in the plant. But to get it certified for use, the smart valve had to undergo a rigorous security audit by the information technology (IT) department at the plant.
Read More
Topics:
Security,
MQTT,
groov EPIC,
cybersecurity,
firewall,
EPIC Security,
EPIC Security Series
Ever notice how emergency exits in a building open outward? Then, to keep the building secure, they are usually locked from the outside. You can get out easily enough, but you can’t get in that way.
However, on a building’s main front entrance, the door often swings in so you can enter. Typically, there is a security guard or perhaps a receptionist there to check your ID and keep an eye on the comings and goings.
Read More
Topics:
Security,
groov View,
groov EPIC,
groov Manage,
cybersecurity,
firewall,
EPIC Security,
EPIC Security Series
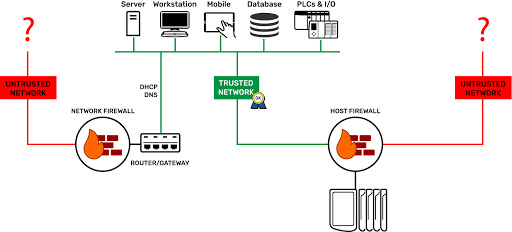
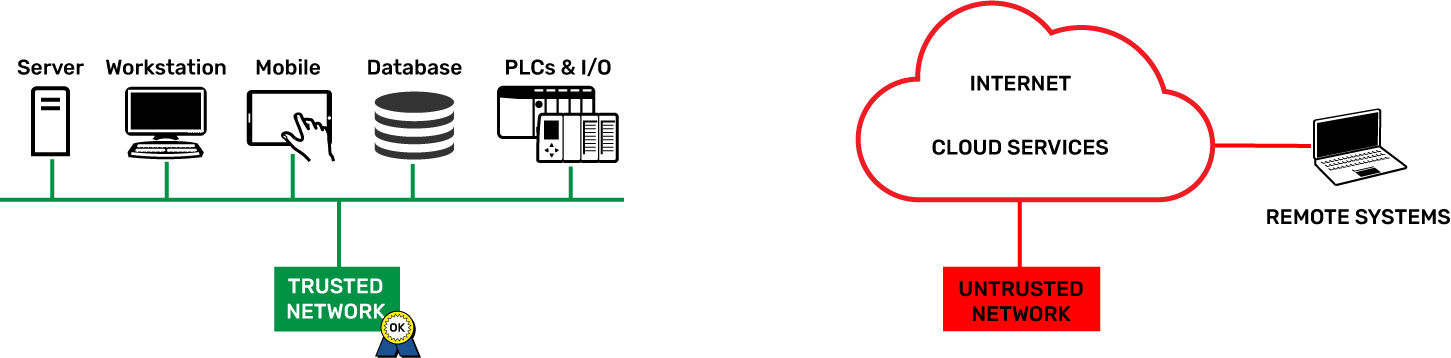
Trusted and untrusted: when it comes to people, it can be hard to know someone at first pass. You need some time to build a picture of the person.
When it comes to networking, it’s a little more cut and dried. You either know who’s on a network or you don’t.
Can it really be that simple? Is there really a way on a groov EPIC to keep those you don’t trust away from those you do?
Read More
Topics:
Security,
EPIC,
groov View,
groov EPIC,
cybersecurity,
EPIC Security,
EPIC Security Series