Ever notice how emergency exits in a building open outward? Then, to keep the building secure, they are usually locked from the outside. You can get out easily enough, but you can’t get in that way.
However, on a building’s main front entrance, the door often swings in so you can enter. Typically, there is a security guard or perhaps a receptionist there to check your ID and keep an eye on the comings and goings.
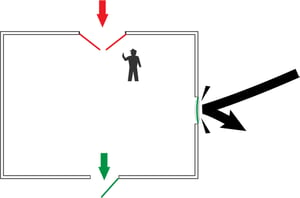
A firewall on a network or a device (a host) is kind of like the doors in a building. Communications can occur outbound from a firewalled network or device, just like people can leave through the emergency exit doors of a building. But communications attempting to come in are rejected, just like people can’t come in through the locked emergency exits.
These inbound communications are only permitted through an open network port, and only with the right encryption and credentials—again, kind of like entering through a building's main entrance door, but only if they have an ID and an appointment to visit someone inside.
The Function of a Firewall
Generally speaking, firewalls stop unsolicited traffic from accessing your network or host and only accept responses to traffic that originally came from the host itself. So, most firewalls permit devices or services behind the firewall to originate and establish communications outbound to external servers or services, while blocking inbound attempts.
This is true for corporate firewalls (network firewalls), and the firewall in groov EPIC (a host firewall). These firewalls block all inbound connection attempts to any internal listening services from outside the firewall—except specific ports configured to allow connections (open ports).
For example, groov View is a software application running on groov EPIC that listens for incoming connections on secure port 443. So, going back to the building analogy, for a connection to be established, a door must be open (firewall port 443), and the person trying to get in must have an authorized ID (username), and the name of the person they're visiting (password) to give to the guard before being allowed entry.
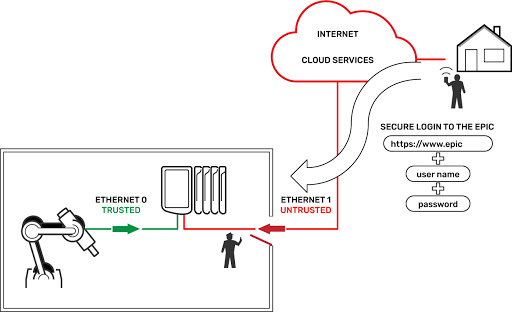
Note that in the groov View example above, the incoming connection on port 443 must be encrypted with TLS (Transport Layer Security), and the first page that is served is an authentication page where the user must enter the correct username and password (more on user accounts in a future blog post).
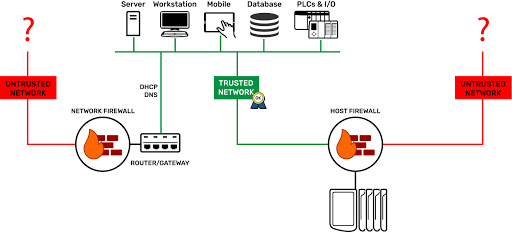
What's the difference between a network firewall and a host firewall?
Perhaps you have tried to get a program or service to work on your Windows PC, only to find that the computer’s firewall was stopping the program from doing its function.
The Windows firewall is a host firewall; it is different from your corporate firewall. One protects a host (a device like your PC); the other protects a network, specifically the hosts and devices on that network.
groov EPIC has its own host firewall, and just like on your Windows PC, you control it. Through the groov Manage web app, you can control which ports, protocols, and interfaces are open for incoming connections to the services listening on each port number.
This is huge. Not only is EPIC one of the few industrial devices to include a firewall; we give you control of it!
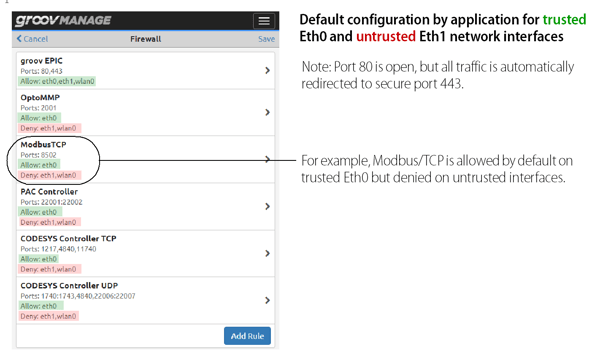
In the groov EPIC’s default configuration, ETH0 (the trusted network interface) has the usual automation protocols and software application ports open—for example, PAC Control (port 22001), CODESYS® (ports 1217, 4840, 11740), Modbus®/TCP (port 8502), OptoMMP (port 2001), Ignition Edge® and Ignition Designer (ports 8043, 8088), and finally groov View (port 443).
Of course, you can (and should) close any of these ports in the firewall settings if you’re not using a given software, or want to prevent access on a given network interface.
ETH1 (the untrusted network interface) has only one port open in the default configuration, and that’s the encrypted and authenticated secure port 443. (Note: port 80 is open and listening, but automatically redirects all traffic to port 443.)
You can see this in the screenshot of the default firewall settings below. Green is open (allowed), red is closed (denied).
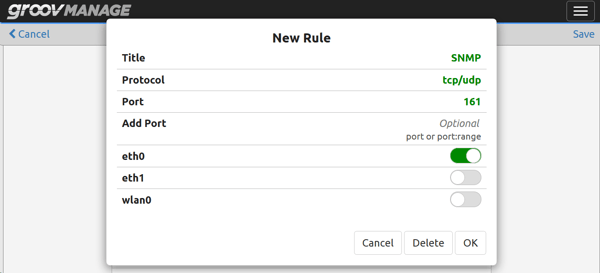
This next screenshot is also from groov Manage and shows that we’re adding a new firewall rule on the EPIC for a new listening service, in this case SNMP (Simple Network Management Protocol). You can see from this screenshot how you can give the rule a name, select the protocol (TCP, UDP, or both), the port, port range, or a number of open ports, and most important of all, you can specify which network interface(s) you want this port open on.
Note that simply opening a firewall port does not also start a listening service on that port number. You have to start a listening service manually or programmatically. For example, in this scenario, opening the port doesn’t start the SNMP listening service.
Wrapping it all up
To oversimplify the functionality of a firewall:
- Firewalls block any requests that did not originate from inside the host or network.
- Firewalls keep track of any outbound connections, so that returning data can be passed back through to the originating service.
- Firewalls can be configured to allow traffic through open ports to listening services.
- Firewalls can also be configured to block traffic through ports you are not using.
By default, groov EPIC helps you build and maintain a secure automation system by providing a host firewall that is set up to allow automation protocols on the trusted interface and only one open, encrypted, and authenticated port on the untrusted interface.
In our next post, we are going to talk about device-originating communications to show how you can bi-directionally exchange data with software and services without opening any firewall ports on groov EPIC at all.
Till then, keep your emergency exits opening from the inside only, and keep your guards on duty.
Cheers, mate!
Want to learn more about security with groov EPIC? Read our technical note, groov EPIC Security Design and Best Practices.
