Trusted and untrusted: when it comes to people, it can be hard to know someone at first pass. You need some time to build a picture of the person.
When it comes to networking, it’s a little more cut and dried. You either know who’s on a network or you don’t.
Can it really be that simple? Is there really a way on a groov EPIC to keep those you don’t trust away from those you do?
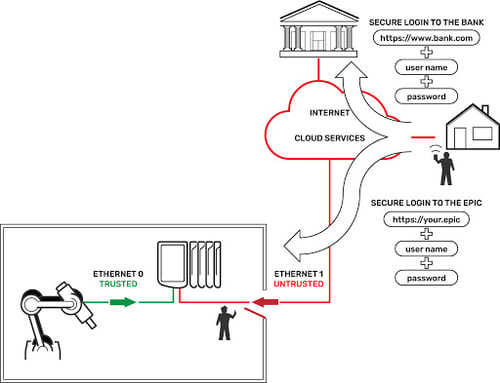
With the dual Ethernet network interfaces on groov EPIC, it can be a straightforward process to keep your trusted networks and untrusted networks from mixing.
Let’s be clear: A trusted network is one where you know who is on it, and you trust them. A good example of a trusted network is your own private network, where only you have access to the network. Or maybe it’s your corporate IT network where your IT department manages users on the network through various tools available to them.
An untrusted network is one where you don’t know who’s on it. A good example of an untrusted network is the internet.
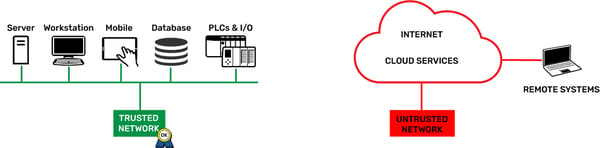
You need to be able to segment these two networks, trusted and untrusted. You don’t want participants on one network to be able to access the other.
The dual independent Ethernet network interfaces on the EPIC exist for a purpose. This practice of separating trusted and untrusted networks is a core security design of groov EPIC, and the two Ethernet interfaces allow you to do it.
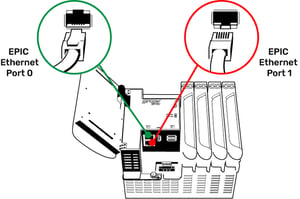 To make these two interfaces independent, and therefore more secure, the EPIC does not permit any routing functions between the two network interfaces.
To make these two interfaces independent, and therefore more secure, the EPIC does not permit any routing functions between the two network interfaces.
A router’s function is to route packets of information between two network interfaces. Routers join two networks together, which is the last thing you want to do in this scenario. You want to keep your trusted network totally isolated from the untrusted network.
groov EPIC can help you do just that.
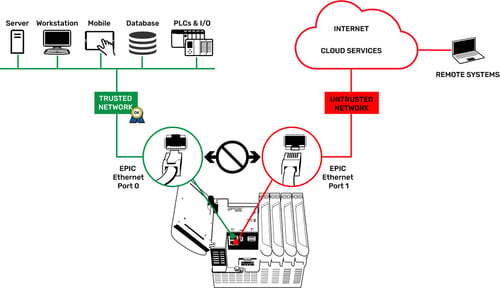
So, which Ethernet interface do you use on which network? In the groov EPIC’s default configuration, ETH0 is designed for your trusted network and ETH1 is for your untrusted network. That makes things clean and simple.
The ETH0 interface is shipped with permissions to access the software and protocols that reside in the EPIC processor. Some of these software and protocols aren’t available with security capabilities like encryption and authentication. One example is Modbus/TCP. It’s wide open and anyone on that network interface can access the Modbus registers at a whim. So, make sure you trust anyone on that network.
The ETH1 interface is shipped with only secure, encrypted, and authenticated access to the software running on EPIC. That means unless you have an account on the EPIC controller, and can create an encrypted HTTPS connection to it, you will be denied access. That’s by design, and why we recommend using ETH1 if you have to place your EPIC on an untrusted network like the internet to allow remote access.
Remote Access from the Internet?!?
Before we go on, let's take a moment to consider the question that might be popping into your head about now: why would I even consider configuring my EPIC’s ETH1 interface to be accessible from an untrusted network, like the internet?
Imagine you have a robotic system working around the clock making widgets for you, and you either want to keep an eye on it after hours, or need to check in on an alert. How do you do that when you are not in your plant on your trusted network?
The answer is: use ETH1 for the untrusted network, which includes a connection to the internet. As we said, in the default configuration, ETH1 permits only encrypted, authenticated connections over HTTPS port 443.
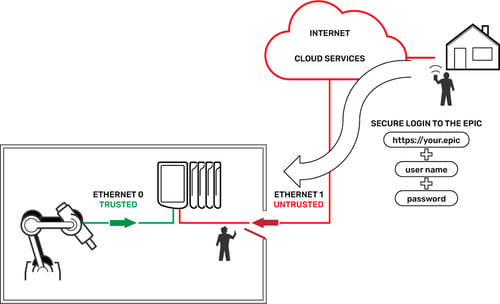
Now you can use your internet connection at home to securely connect to your EPIC in the plant over HTTPS, log in with your username and password, and “surf” to the groov View software's robot screen to view its status. (This of course assumes your IT department will permit incoming requests through the corporate network firewall on secure HTTPS port 443. More on this topic coming in Part 2 of this blog series.)
It’s kind of similar to how you bank online: you use an encrypted and authenticated connection over the internet to your bank to check your account. In the robot system example, you use the same type of connection over the Internet to your EPIC controller at the plant and check the robot.
"Ain't gonna do it!"
Now this scenario isn't for everyone. Despite the security features built into the groov EPIC to allow a secure connection from untrusted networks like the Internet, there will be objections to the idea from the get-go. It might be your IT department, who isn’t willing to open port 443 on their firewall to permit the inbound connection to your EPIC. Or maybe you’re just psychologically opposed to the notion of any control device connected to the internet.
No worries. We’ve got a solution for you using publish/subscribe architecture, which we will describe in a future blog.
Keep in mind you are in complete control. It’s your EPIC. We’ve designed EPIC with its factory default configuration to be as secure as possible, helping you architect a system you can feel good about. But you do have the power to alter the default configuration and use these dual Ethernet interfaces in any way you wish. Reminds me of Spiderman’s Uncle Ben, and his famous quote: "With great power comes great responsibility."
In the next blog, we’ll take a closer look at the firewall that protects groov EPIC’s ports and how it adds another level of network security to your system.
Cheers, mate!
Want to learn more about security with groov EPIC? Read our technical note, groov EPIC Security Design and Best Practices.
Other posts in this series:
- Part 2: What's a firewall?
- Part 3: Device-originating communications, or how and why MQTT rocks
- Part 4: User accounts
- Part 5: Encryption and certificates
- Part 6: Linux operating system and repository
