The OS, or operating system, of groov EPIC is very different from traditional controllers. Instead of a proprietary OS, EPIC uses an open-source Linux® operating system.
From a security standpoint, an “open source” OS sounds scary. But in many ways it is more secure than a closed-source one, especially a well-known and often-attacked OS such as Microsoft® Windows®.
One of the advantages of open source is that it means crowd sourced. Open-source software is largely used to power the internet, and a worldwide community supports the code base. Because of the huge number of developers working on Linux, vulnerabilities tend to be addressed very quickly and thoroughly. That’s the power of the crowd. With such a large number of developers viewing and developing the source code, safer and more reliable software results.
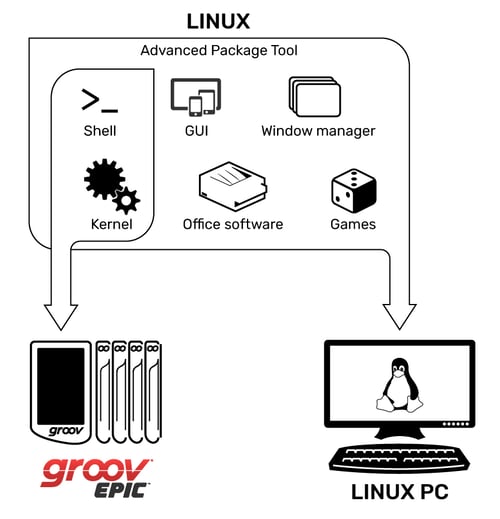
The open-source nature of Linux can also be less open than you might think. In other words, there are several custom distributions of Linux in the world today for very specific devices.
If you’re not familiar with it, the Yocto Project is a multi-vendor initiative that was started in late 2010. It is not a Linux distribution itself; it’s a tool set. It provides the means and methodologies for developers to create custom-made Linux distributions for their embedded Linux hardware. It’s still Linux under the hood, but it’s not the typical Linux approach of “one size fits all.” Instead, it’s purpose-built for a specific device.
“The easiest vulnerability to address is the one you don’t include,” noted Ryan Ware, Security Architect at Intel®, in 2017.
That’s exactly why we use a Yocto Project build of Linux in groov EPIC. Our Yocto build is custom built just for the groov EPIC, and we include only the packages required for EPIC functionality. Leaving out all unneeded packages reduces attack vectors, because every application you add makes it more difficult to keep your installation secure, stable, and up to date.
On top of all this, the Yocto build of EPIC Linux (basically, the EPIC's firmware) is cryptographically signed with the Opto 22 Private Key. (See our blog post on encryption and how certificates work for more about private keys.) This cryptographic signature proves that it’s been built by Opto 22 and guarantees that the firmware has not been altered or corrupted since it was signed.
Any firmware or software package anyone might try to upload to the EPIC must be Opto 22 cryptographically signed, or the processor will not accept it.
It’s interesting to note that Linux generally does not use code signing, since its open-source nature lends itself to code inspection. However, Opto 22 has chosen to use code signing to protect the EPIC, because it is a control system.
If you’re a developer using Secure Shell access (SSH) with groov EPIC, you may notice that the software repository (or repo), seems smaller than you expect. The repo is where code packages are stored so developers can pull them in order to build their custom applications. Because all code has been signed by the Opto 22 key, the repo may seem smaller than usual, but it is safer.
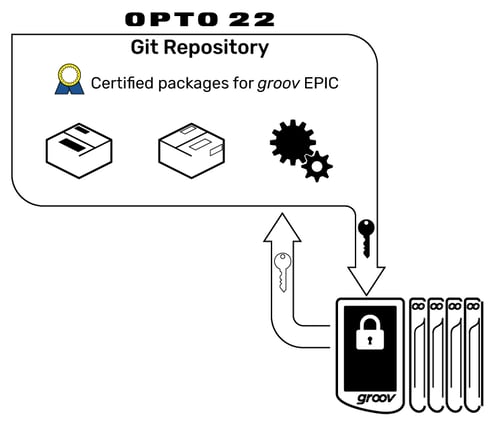
Usually a shell command like ‘apt-get’ is used to download and install the required function from the repo. ‘Apt-get’ still works exactly the same for groov EPIC, but it checks only the Opto 22 repo and pulls only software that has been known to work with the groov EPIC system. Of course the repository is not static; we add to it as needed for each groov EPIC firmware update.
Put all this together and the raw power of the Linux OS gives groov EPIC a very long life with room to grow in the future—and all the while helping you build a more secure system.
Till next time. Cheers, Mate.
