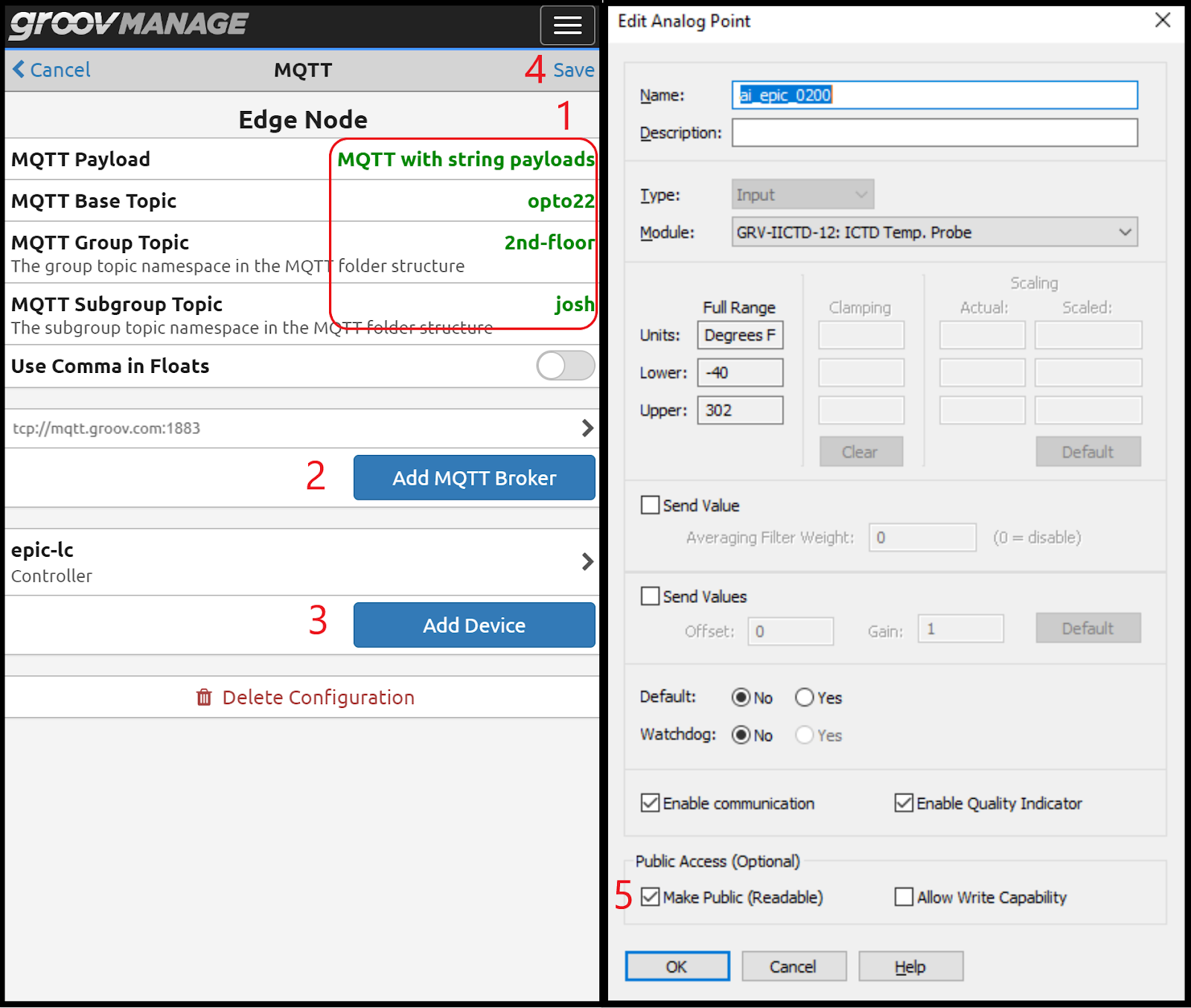
The recent announcement of security vulnerabilities discovered in the Wind River® VxWorks® IPnet TCP/IP stack has prompted questions from Opto 22 customers about what impact this discovery may have on TCP/IP-based products developed and manufactured by Opto 22.
Opto 22 would like to reassure our customers that, after careful and thorough review, we can state that none of our hardware or software products contain the VxWorks IPnet TCP/IP stack or variants of that software and are, therefore, not directly exposed to any attacks that might target these vulnerabilities. This statement applies to the recent Opto 22 product family groov EPIC® (edge programmable industrial controller), the groov® Edge Appliance (groov Box), the SNAP PAC® System, and SNAP Ethernet I/O® products.
These security vulnerabilities, dubbed URGENT/11 by Armis, an enterprise IoT security firm that made the discoveries, have far-reaching implications and affect an extremely large array of industrial, medical, and enterprise environments. These include mission-critical systems such as SCADA, industrial controllers, PLCs, PACs, and more. Other systems outside traditional industrial devices like patient monitors and MRI machines, as well as firewalls, routers, modems, VOIP phones, and printers are also affected.