In this blog post, let’s take a closer look at user accounts on the groov EPIC system, and how you can improve your system security by giving users and services fine-grained access to applications running on EPIC. In other words, make sure each person or service has only the access they really need and nothing more.
But before we get deep into user accounts, let’s first discuss user account credentials. Take a moment and ask yourself the following questions:
- Do you use the same password for multiple accounts?
- Do you use a mix of punctuation and capital letters in your passwords?
- Do you use long phrases as your passwords?
Read More
Topics:
Security,
groov View,
groov EPIC,
groov Manage,
cybersecurity,
EPIC Security,
User Accounts,
EPIC Security Series
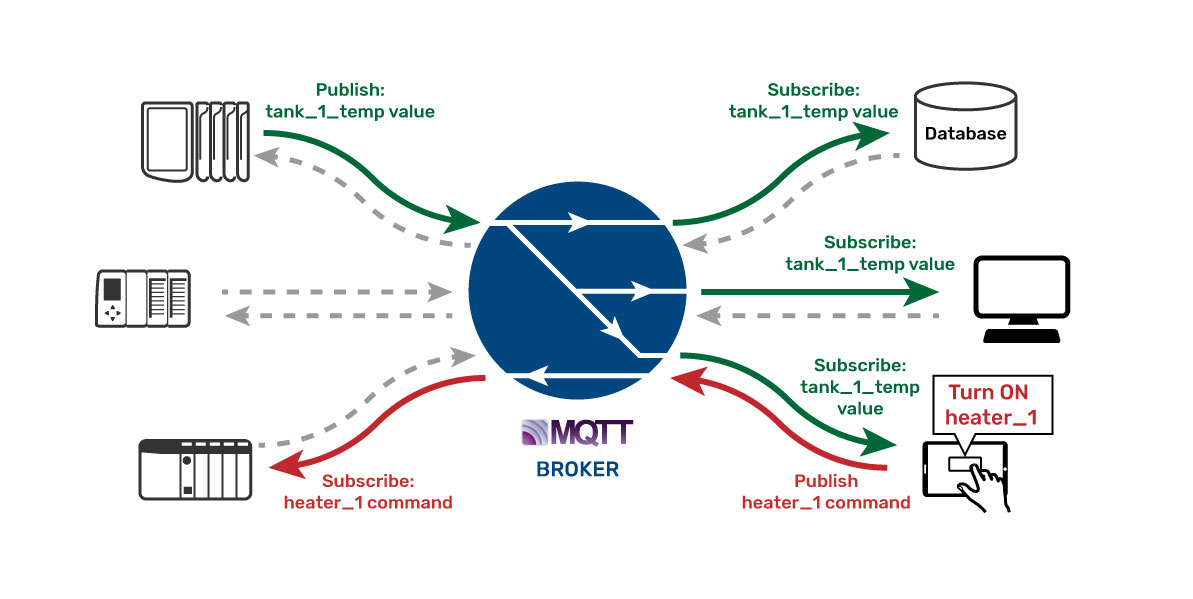
The story goes that a valve manufacturer wanted to have their networked smart valves certified for use in a nuclear reactor plant. The smart valve could report all sorts of critical data points to a database system and also be controlled by that SCADA system in the plant. But to get it certified for use, the smart valve had to undergo a rigorous security audit by the information technology (IT) department at the plant.
Read More
Topics:
Security,
MQTT,
groov EPIC,
cybersecurity,
firewall,
EPIC Security,
EPIC Security Series
The 32nd annual Control Engineering Engineers’ Choice Awards shined a light on 26 categories of control, instrumentation, and automation products, revealing the best of those introduced in 2018. Winners were voted on by the Control Engineering magazine print and digital audience. As announced earlier this year, Opto 22's groov EPIC was the award winner in the Industrial Internet of Things connectivity category.
Read More
Topics:
Awards and recognition,
Security,
EPIC,
groov EPIC,
white paper
Ever notice how emergency exits in a building open outward? Then, to keep the building secure, they are usually locked from the outside. You can get out easily enough, but you can’t get in that way.
However, on a building’s main front entrance, the door often swings in so you can enter. Typically, there is a security guard or perhaps a receptionist there to check your ID and keep an eye on the comings and goings.
Read More
Topics:
Security,
groov View,
groov EPIC,
groov Manage,
cybersecurity,
firewall,
EPIC Security,
EPIC Security Series
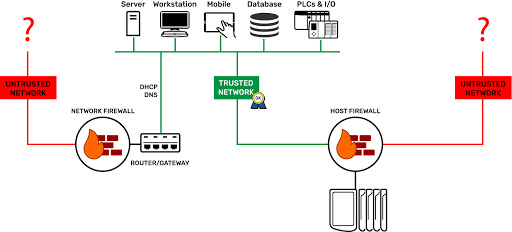
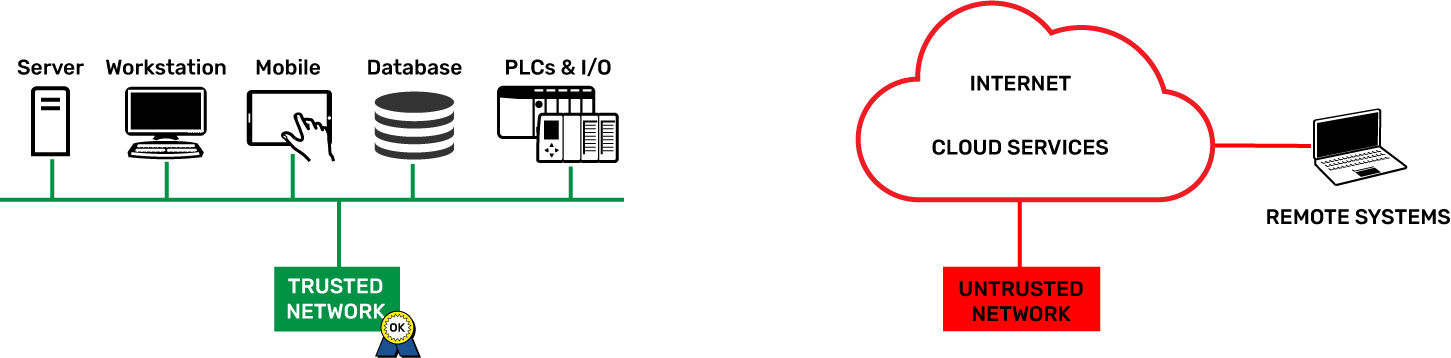
Trusted and untrusted: when it comes to people, it can be hard to know someone at first pass. You need some time to build a picture of the person.
When it comes to networking, it’s a little more cut and dried. You either know who’s on a network or you don’t.
Can it really be that simple? Is there really a way on a groov EPIC to keep those you don’t trust away from those you do?
Read More
Topics:
Security,
EPIC,
groov View,
groov EPIC,
cybersecurity,
EPIC Security,
EPIC Security Series
Looking to learn more about IIoT technologies, control systems, and how they work together? It’s time to check out OptoU!
This free online training program provides convenient, on-demand training courses to fit in with your busy schedule. With its “watch and learn” premise, course topics are made up of video and written lessons. The secure sign-in feature lets you return to unfinished lessons and learn at your own pace.
Read More
Topics:
PACs,
Networking,
Training,
I/O,
Security,
IIoT,
Industrial Internet of Things,
Node-RED,
MQTT,
Ignition Edge,
EPIC
Would you like to know more about the new groov EPIC system?
Now you can, on your own schedule.
- Learn how to simplify your automation and IIoT projects.
- See how to improve security and performance, with minimal reliance on IT personnel.
Read More
Topics:
Webinars,
groov,
Internet of Things,
IoT,
Machine builder,
OEM,
New products,
Integrators,
Security,
IIoT,
Industrial Internet of Things,
Data acquisition,
EPIC
Undoubtedly you’ve heard of the most recent ransomware attack plaguing the globe. It started late last week and so far has infected machines across 150 countries.
As the name suggests, the virus in effect holds the infected computer hostage and demands that the victim pay a ransom in order to regain access to the files on his or her computer. You can learn more about ransomware in this previous blog post.
But let’s get down to what you need to know. Here are the latest facts about WannaCry that you need to be aware of to make sure your systems are not at risk.
Read More
Topics:
Security
As the IIoT continues its widespread adoption, a lot of new IT technologies are quickly being adopted by the industrial automation and process control industries. More and more, industrial assets are becoming Internet enabled and being connected to other digital systems.
Monitoring OEE and KPIs in real time from a mobile device is no longer a pie-in-the-sky application. It’s happening right now, through the convergence of OT and IT.
One of the technologies that’s enabling the IIoT is secure digital communication. And to establish that secure communication, you need to have an authority you can trust that can validate the indentity of devices on a network and on the Internet. You have to trust that the encrypted connection you're using is actually connected to the device you want to talk to, and not to some rogue node trying to breach your network and steal your information.
That’s where Certificate Authorities come into play in the IIoT.
Read More
Topics:
Process control,
Internet of Things,
IoT,
PACs,
Security,
IIoT,
Industrial Internet of Things
In a previous blog post we covered what ransomware is and how it’s being used to target industrial users like water and wastewater SCADA systems.
Ransomware is basically when a hacker obtains control of your data, or even your control network and automation systems, and won’t relinquish control back to you until a ransom is paid.
It's a major potential threat against IIoT applications.
Read More
Topics:
PACs,
Security,
IIoT