Tale of two LANs
Would you like to view critical plant status from anywhere on the Internet?
Are you worried that if you connect your automation network to your company’s IT network (which is likely connected to the Internet), the wrong people could access your control system? Or that traffic like YouTube might impact your automation network throughput?
There are a lot of advantages and only a few disadvantages to segmenting your IT (Information Technology) network from your OT (Operational Technology, in other words your controls) networks. While there are a few different ways to segment networks, in this blog we are going to look at separating them using one of two Opto 22 products: SNAP PAC Controllers and groov.
Segmenting your LANs
Keeping your company network (IT) isolated from your automation network (OT) adds a layer of security (also sometimes called an air gap). With your IT network on a different physical network segment from your OT network, normal network traffic will not be able to flow between them. In other words, they will be isolated, and neither will see any of the other’s network traffic--broadcast or otherwise.
What do segmented networks even look like? Imagine two circles that do not overlap. Each circle is a network. Traffic can flow inside each network, each is fast and totally isolated from the other, and since they are not connected in anyway, each is secure. If only the IT network has Internet connectivity, then even if it is compromised, there is no way anyone can connect to, view, or otherwise interfere with the OT network.This added layer of security comes with a downside: you cannot view any automation data while on the IT office LAN. Also you cannot make any changes to factory or automation systems while you are sitting at your desk in the office. You need to go to where you have physical access to the automation network. As we have mentioned in past blogs, if it’s easy, it’s not secure.
What if you want to connect the company email server from the automation network to send emails or texts for an out-of-band condition? Or what about viewing data and having authenticated, customized control over the automation devices on your OT network from the IT network? Is there a middle ground here somewhere?If you need to add visibility into either network, you can, by adding a dual network hardware device that is not a bridge, switch, or router, but rather offers data visibility to both networks on a variable-by-variable basis.
Scenario #1 - Using a PAC to Segment your LANs
You can use the two Ethernet ports on a SNAP PAC controller to segment two networks, in this scenario, the IT and OT networks.
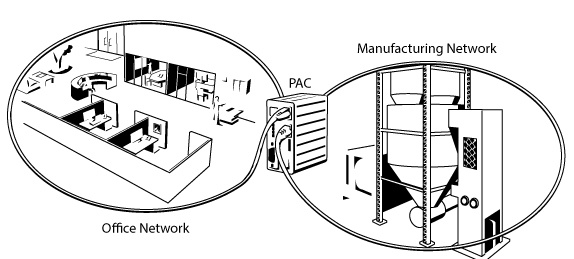
You can view any of the automation data you specify using PAC Display on the company network, and have full automation control on the other network. Since the PAC controller is not a bridge or router, there is no way to have any rules or conditions that could be leveraged to compromise the automation network from the company network.
The PAC controller can be configured to test any variable and email you if it goes out of range. It can do this because one interface can "see" the data, and the other interface can send the email to the server. It cannot receive email, so spam is not going to be an issue.
Scenario #2 - Using groov to Segment your LANsYou can also use the two Ethernet ports on a groov Box to segment two networks.
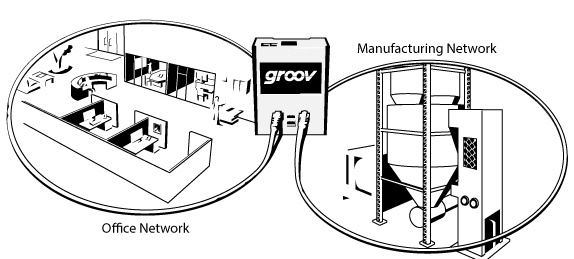
You can traverse the two networks’ data using groov screens. By setting up different groov user accounts with username and passwords, you can provide exactly the right level of data that each person requires. For example, someone in the office can view their groov screens from the IT network, and the automation guys can view their groov screens on their OT network.
In this case, the office groov user might only have a few view-only screens that do not have any control gadgets on them. Meanwhile, the automation guys’ groov user account may have full access to the whole process through a series of in-depth screens that include monitoring and control.
Using groov to send an email or text is very powerful, and simple to configure. An authorized user simply configures the condition they wish to be notified about through the Event Manager in groov Build, and groov will take care of the rest.
The same principle applies using groov Server for Windows. PCs support dual network cards and so they can be used to segment the IT and OT networks, exactly like the groov Box does.
Check out the Networking Opto 22 Products (PDF) guide for a lot more technical information on segmenting networks (and more).Segmenting networks adds security.
If you keep your automation network completely disconnected from any Internet access, you keep it secure. You would need physical access to the building and network in order to gain access to any of the devices on the automation network. The downside is that once you leave the building, you can’t access any data screens.
However, if you segment the network, and let groov or a PAC create the bridge between the two, you can safely add a way to view all the data you want and control as much or as little of the process as you like. You are in control of the balance between easy and secure.
Next week we wrap up this whole series and show how the key to having a secure network is not by any one method or device, but by using different layers of security.
Till then, cheers mate.
