Layers of security:
I wish there were, but there just isn’t.... There is no one device, hardware, or software that is the single defense for all known and future network attack vectors—including the one critical weakness: humans. You know, some thing or device that you could simply put at your network's front door and have it reject all the bad guys, but allow the friendlies in without question. Secure and easy is still a wish.
The solution then really comes down to layers. Adding layers that each will take a lot of time and a lot of effort to peel back, so much so that most attackers simply give up and move on.
The past few blog posts have talked about some of those layers, so let's now put it all together and see just how we might go about building a very robust mobile-accessible industrial automation network.
If it's easy, it's not secure:
The main advantage of putting some automation data on your mobile device or making it visible over the Internet is to make your life easier and more productive. From that aspect, then, we are going to have to make some choices. There is going to be a sliding scale between a system (network) that is super easy to use because it is wide open, vs. a system that is so locked down you never use it because it's just too much of a drag. (But, hey, it sure is secure!).
Add more locks, make it safer, but harder to use... here is a picture of the balance you are going to strike.
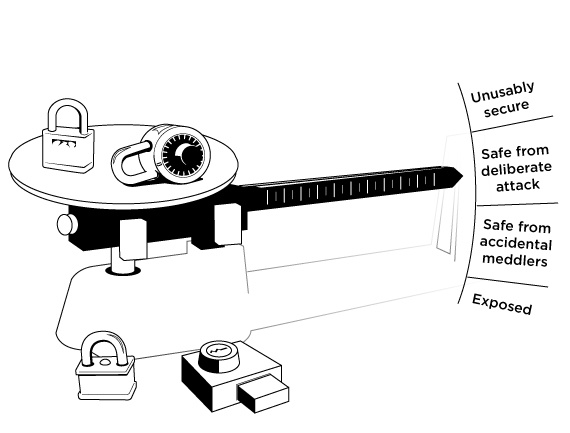
How then do we find that sweet spot?
Let's quickly go back over the past few weeks' worth of blogs to get a feel for some of the layers that we can use to help us find our personal sweet spot between secure and easy.
First up, we talked about passwords and passphrases. The longer the passphrase the more complex it is, and the longer (and more energy) it is going to take to crack. If your passphrase has around 20 to 25 characters you are looking at needing around 500 years to crack it.
Next, we looked at 5 ways to secure a Wifi network. The bottom line there was to use a solid passphrase (that is, strong authentication) and good encryption.
The next week, we talked about securing your mobile device. Again, using a good password, PIN, or complex swipe pattern to lock the device is the first line of defense. We also suggested that you use a VPN (Virtual Private Network) to connect to the network that has the groov behind it. Remember to use to a long passphrase to secure that network as well, and don’t store the passphrase on the phone.
We then talked about how groov uses both authentication and encryption. You have to log into groov with a username and password over an HTTPS connection to view your screens. This means that the login page is encrypted, with a valid certificate; so there can be no man-in-the-middle sniffing of the login details.
Lastly, we talked about how you can segment your two main networks and only connect them through a device that does not allow normal traffic flow, but allows you to choose what specific information is visible on each network.
Walls, lots of walls.
We now have a clearer picture of some of these layers.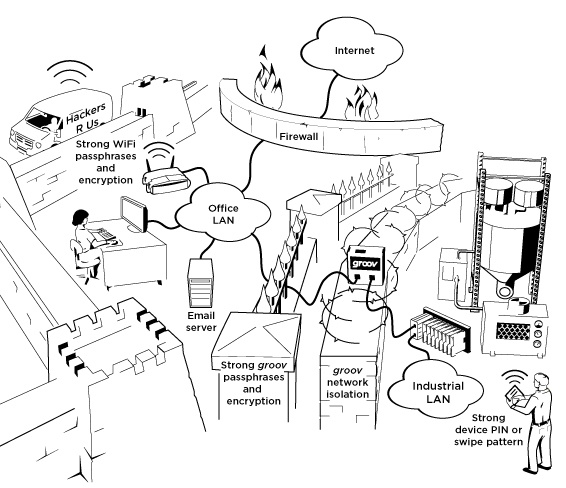
As you can see, by adding layers of strong passphrases and strong encryption, we can build barriers between the bad guys and the high-value target (the automation network). But at the same time, we are able to view the exact data we want from anywhere inside the facility and from anywhere outside the facility. We can also be notified anytime a given condition on the plant floor goes out of band.
Keep in mind that if some person simply gives out the passphrase, some of the walls can come tumbling down. Humans are often the weak link, and we all need to play our part in keeping those walls intact!
We have a very helpful "Networking Opto 22 Products" guide that is worth reviewing if you are looking to do any of this work.
Six part blog on network security.
So there we have it. A customer asked me via Twitter if I could blog about network security and how to add groov in the most secure way. It took the past 6 weeks to fully cover the topic, but hope that you found it helpful.
Be sure and let me know what you would like covered in this blog, I would love to talk about stuff that you are interested in!Till next week, Cheers Mate.
